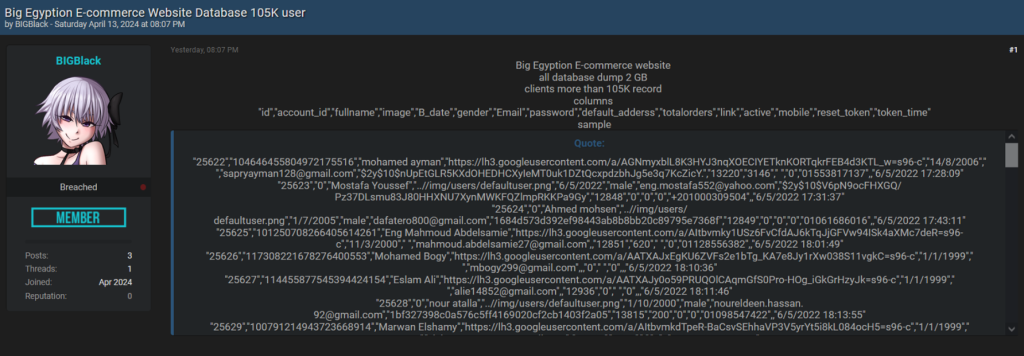
On 13th April 2024, a threat actor named “BIGBlack” Posted a thread on a Darkweb forum titled “Big Egyptian E-commerce Website Database 105K user.”
We gathered Dark Atlas Squad on a group call to initiate our investigation.
Our goal was to determine the victim’s identity and the root cause so we could contain the situation.
We downloaded the added sample and analyzed it on the TA’s thread.
We extracted the potentially important data that would be helpful in our investigations, such as:
“FullName”, “image”, “Gender”, “Email”, “default_adderss”, “total orders”, and “Mobile”
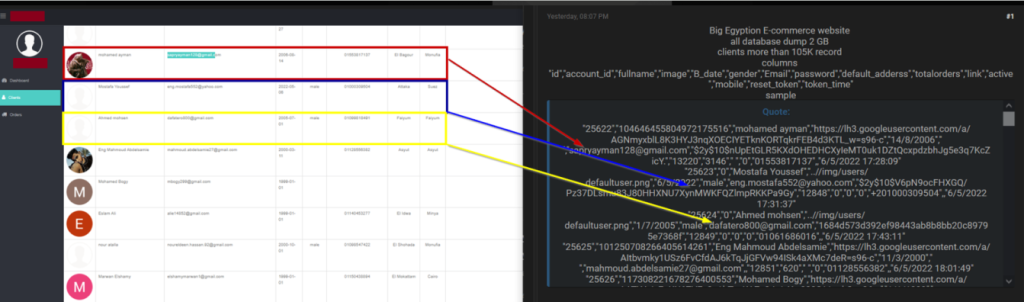
We analyzed a random record in the sample.
We searched with the customer’s email address in our Dark Web Monitoring Solution, “Dark Atlas,” and discovered that he was infected by Information Stealer Malware “Lumma” in 2024.
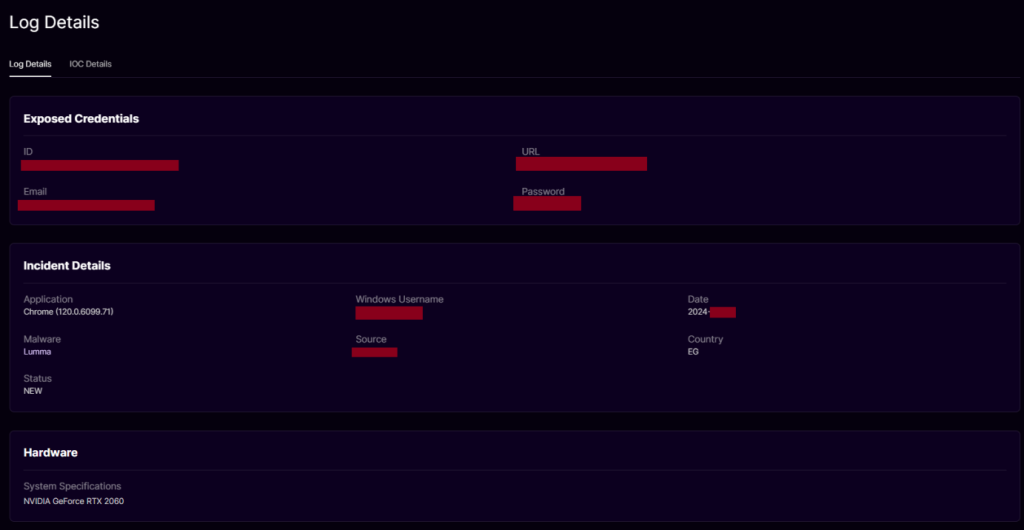
We exfiltrated many records/credentials from the customer’s exposed device and then filtered all the Egyptian E-commerce websites.
We created a decent list but still need more filtration to narrow our investigation scope.
After analyzing the sample again, we noticed that if the user added a profile picture, he would have a custom link for it.
But in the other case, if the user didn’t add a picture, the system will assign him a default picture with the following path:
“/img/users/defaultuser.png”
We crafted a small script to try this path on all the suspected company lists, and Voilà—we got a match!
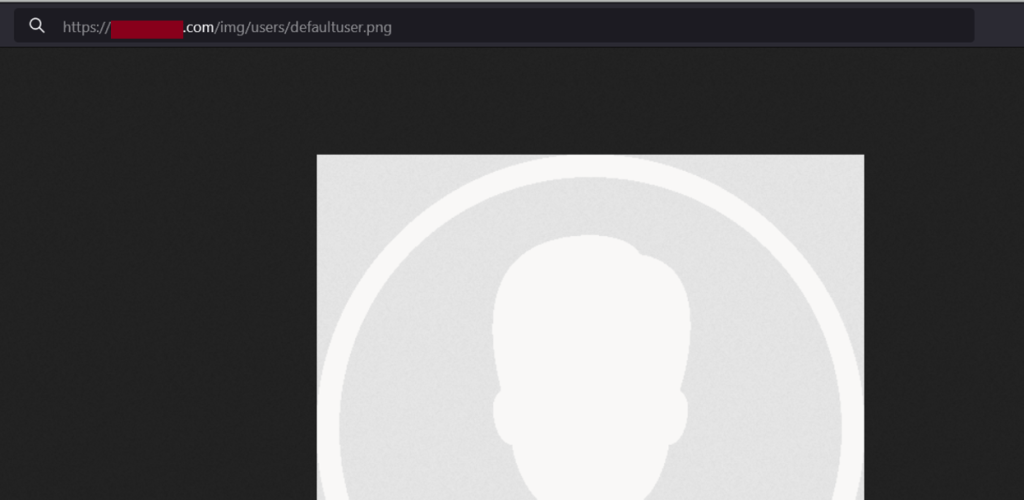
After checking out the website, we saw another proof: the threat actor mentioned the same number of customers on the original thread: +105k.
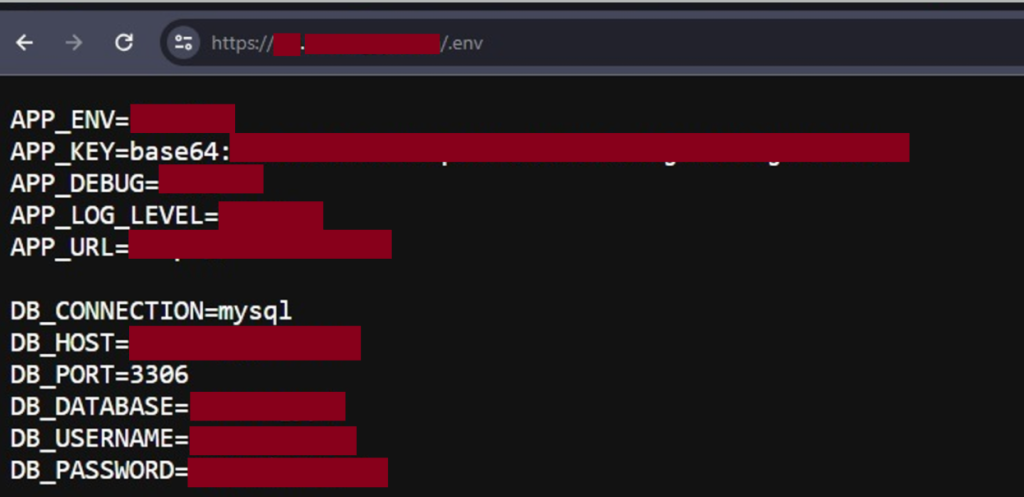
We did a quick security test for the company. In a few minutes, we discovered a forgotten .env file on one of their subdomains containing the MySQL Credentials with a remote connection allowed.
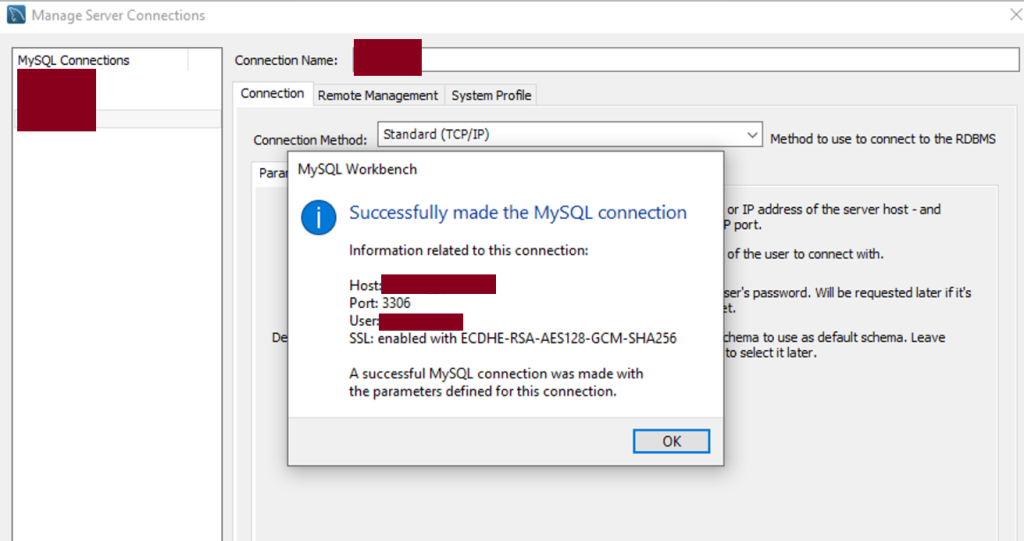
We tried the credentials, and they were indeed valid.
So, the last step to close the investigation was to verify the leak. We quickly searched the client’s data in the database, and all the shared samples matched the existing data.
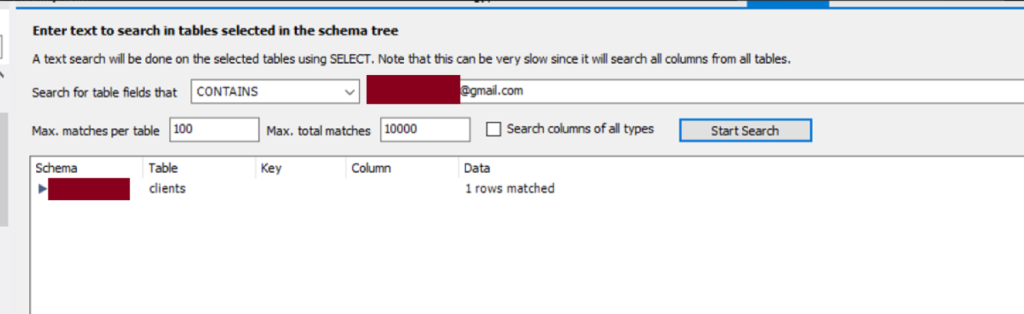
We were able to view all the clients directly through the database connection.
We wanted to take another step in the investigation to avoid neglecting any side.
We searched for compromised credentials for the company’s employees through Dark Atlas, and we successfully discovered a compromised valid account exposing the company’s admin panel with full access.
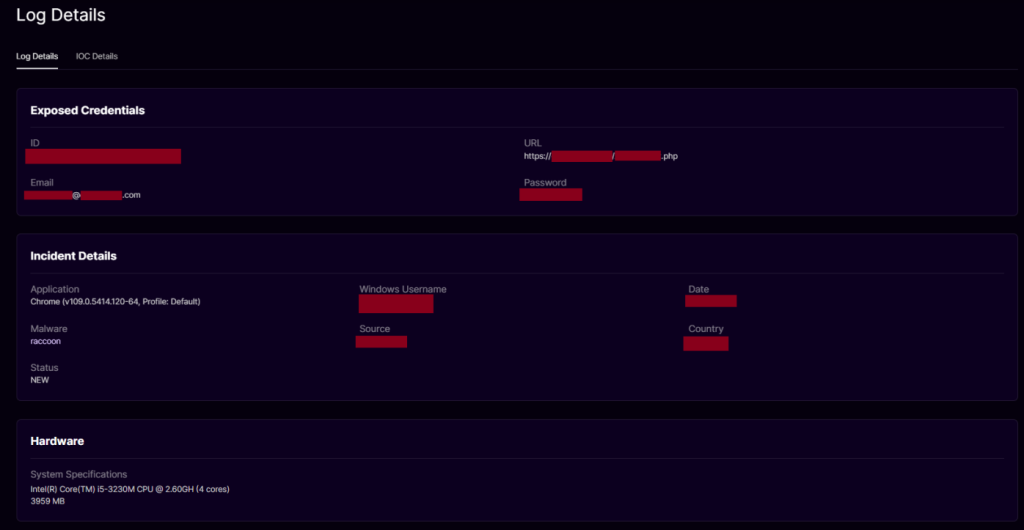
We contacted the affected company, shared all the findings, and confirmed the fixes with them.
Thankfully, they gave us permission to publish our investigation report with you.
Thank you all for reading.
Follow Dark Atlas Squad on Twitter to stay updated.



No Comment! Be the first one.