On June 18th, we observed a lot of security news about “ONNX phishing-as-a-service (PhaaS),” a new product from an old threat actor known as “MRxC0DER,” previously associated with the “Caffeine Phishing Kit.”
Dark Atlas Squad initiated a thorough investigation into this threat actor, focusing not only on his infrastructure but also on his overall activities.
We started by performing Surface-Web Dorking using his username and alternative names.
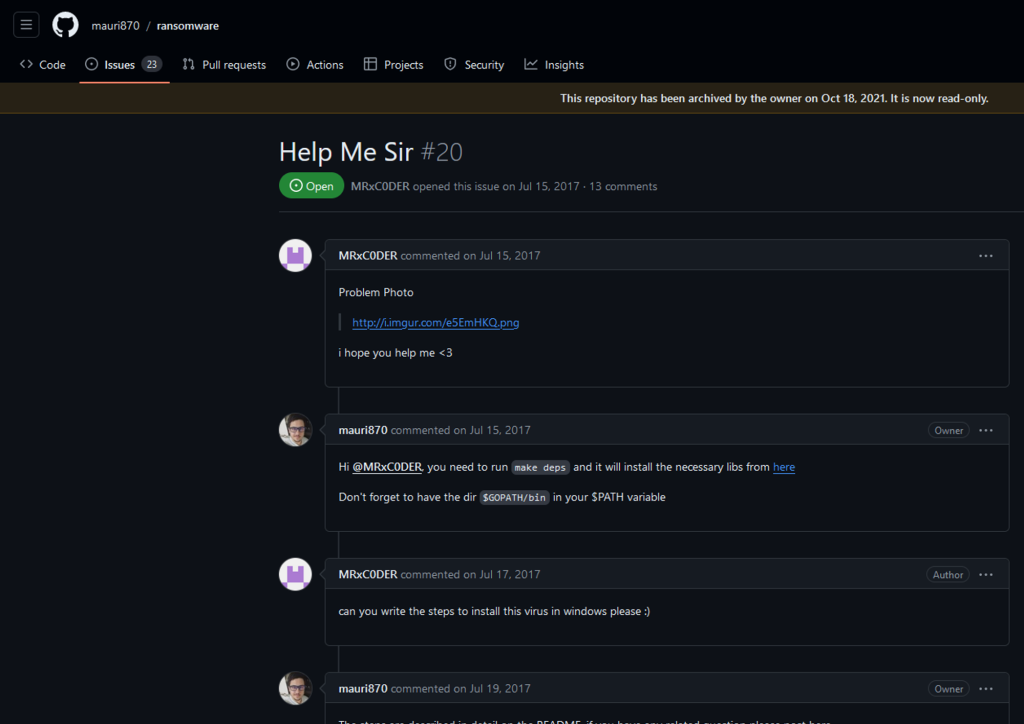
We found a hit on GitHub for the username “MRxC0DER.” The account was mostly empty, except for one issue that opened in 2017, titled “Help Me Sir,” which was related to a ransomware problem.
Further investigation led us to any.run, where we discovered that “MRxC0DER-EG” had uploaded a ransomware sample from his computer. The “EG” in the username likely indicates his nationality.
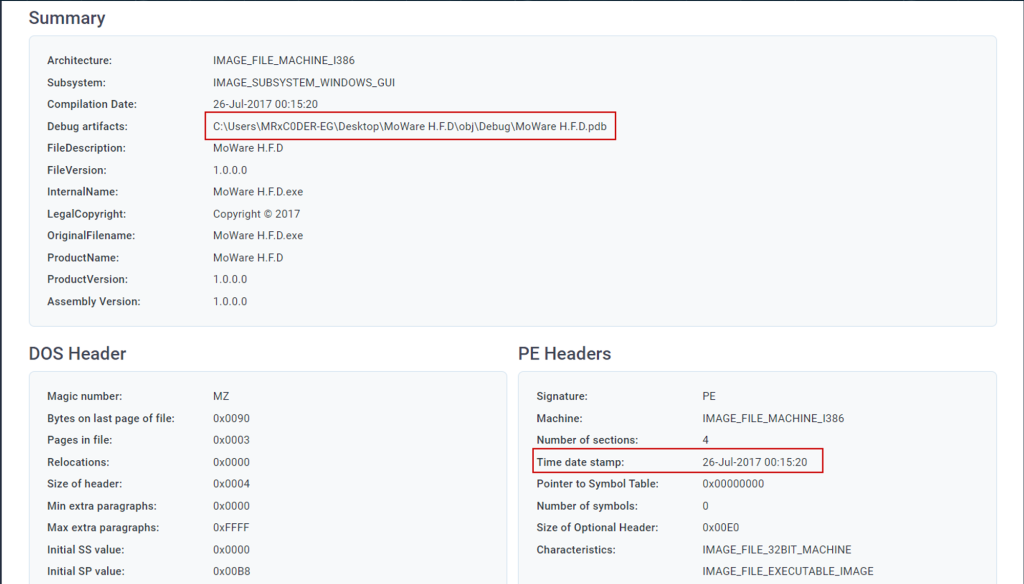
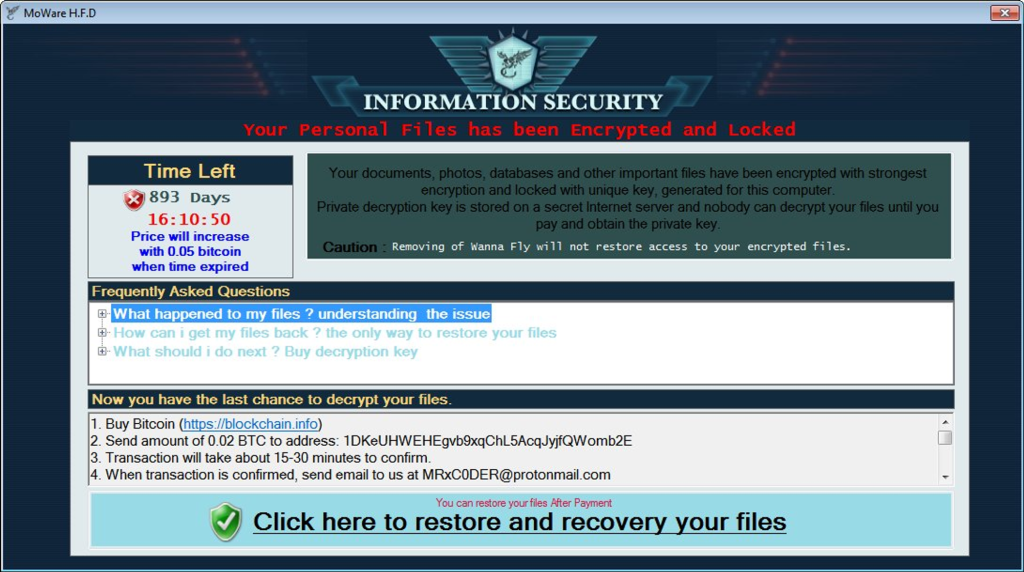
The threat actor deployed and spread his ransomware version in 2017.
We also conducted Dark-Web Dorking using his username in the DarkAtlas.io InfoStealer Malware Logs database and found a match.
Other security companies mistakenly thought this device belonged to the threat actor and revealed his identity, which was incorrect.
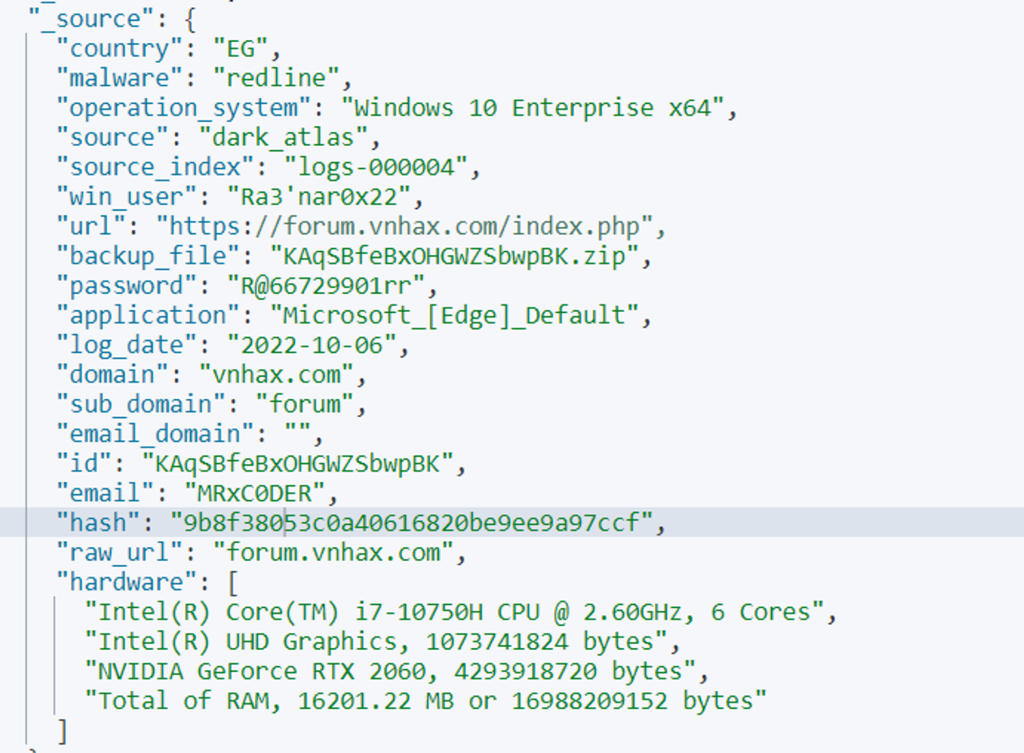
Further investigation revealed that this device belonged to an Egyptian affiliate, “A.G” (Identity Masked)
During our investigation, we found an account on Zone-H with the same username. The account’s last activity was in 2019, including his name and an associated domain.
The “EG” in his defacement index further confirmed his nationality.
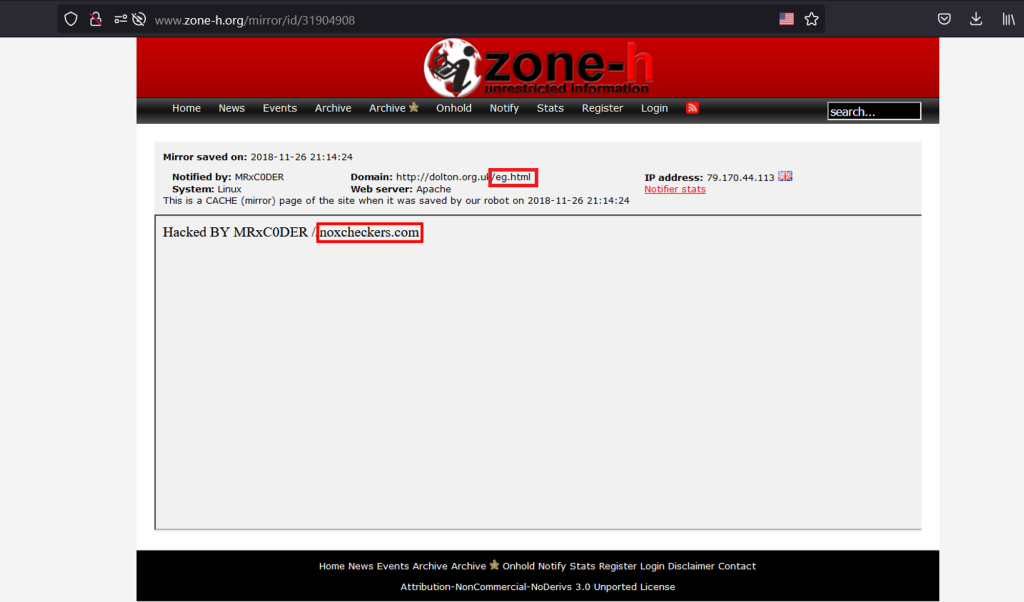
After examining the domain history of noxcheckers.com, we discovered it was hosted on GoDaddy and owned by an Egyptian.
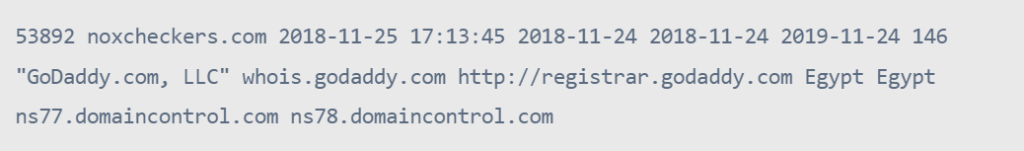
We also searched underground forums and found a match for the same username on the Nulled forum, which has been active since 2017.
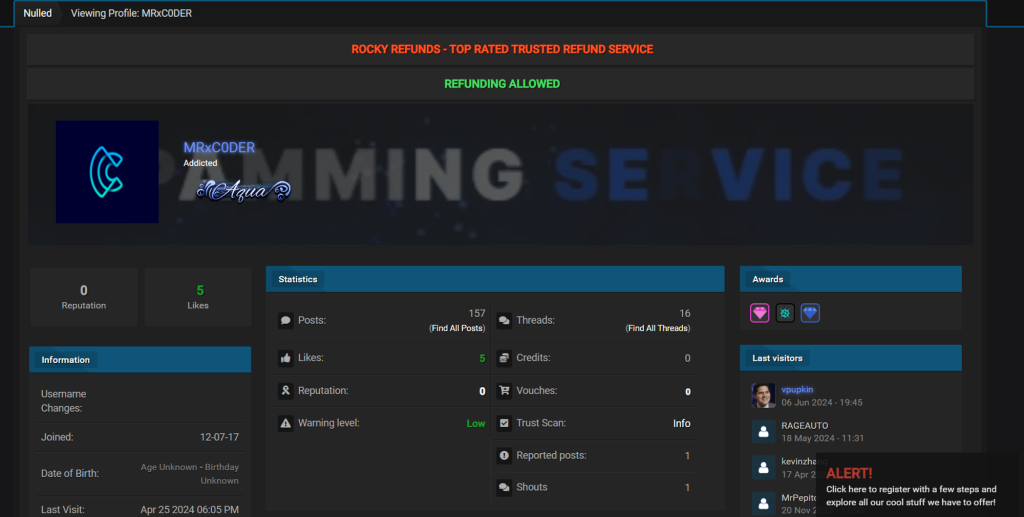
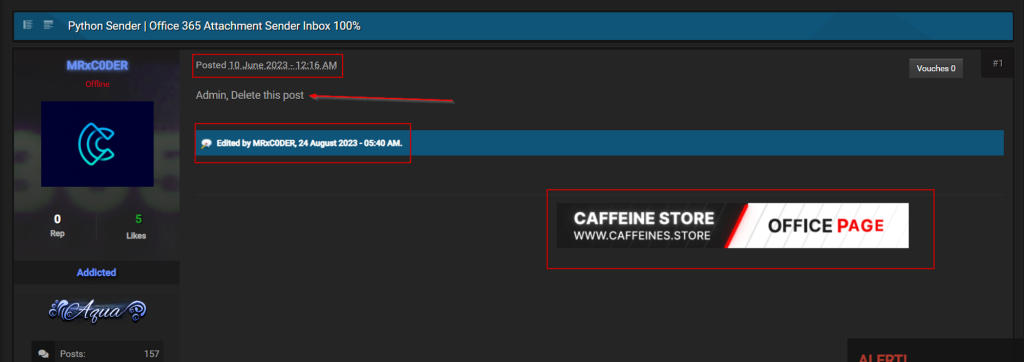
On June 10, 2023, he posted a thread on Nulled advertising his phishing kit “caffeines[.]store.”
He later edited the thread and requested the admin to delete the post, which occurred after he gained attention in security news.
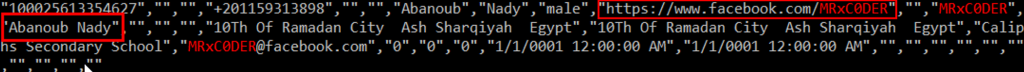
Next, we searched on social media for his nickname and found a matching account on Facebook scraped data. This gave us his phone number, country, address, city, and full name.
Also, we noticed that he disabled this account.
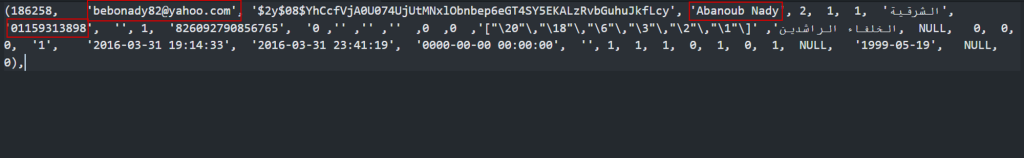
We also searched his phone number for public data breaches and found that his information, including another personal email, was exposed in a breach at nafham.com.
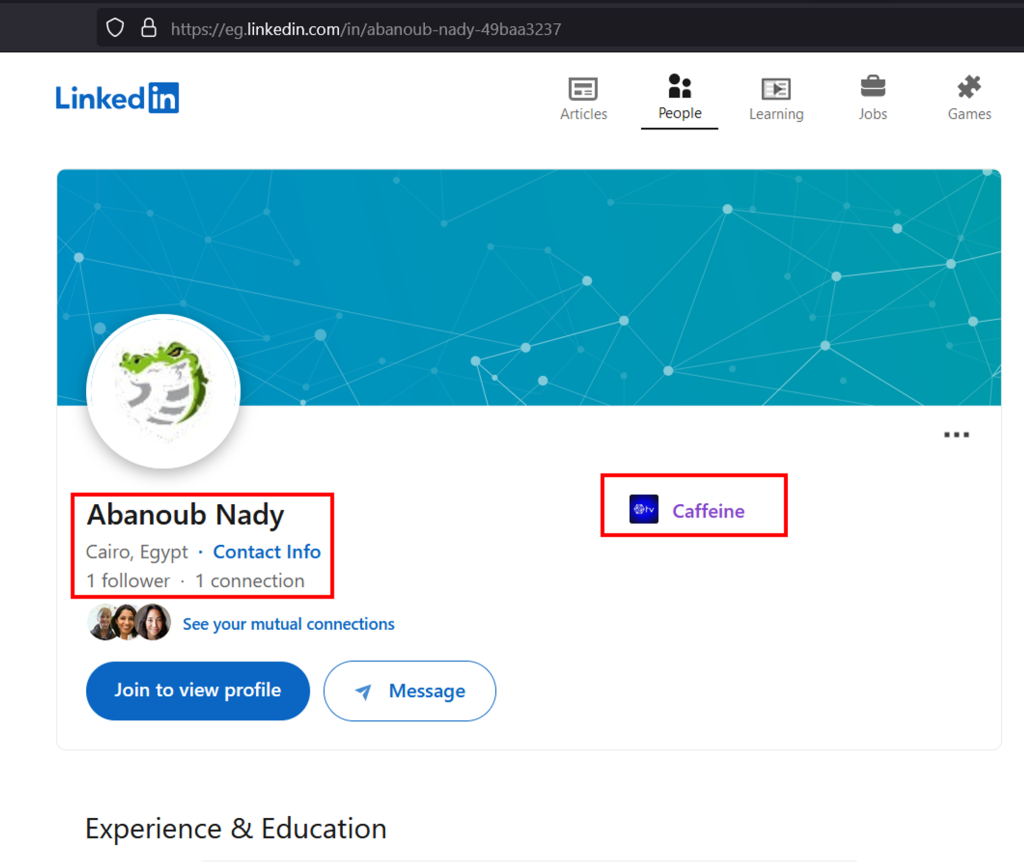
Using the collected data, we created some indicators leading us to his LinkedIn account.
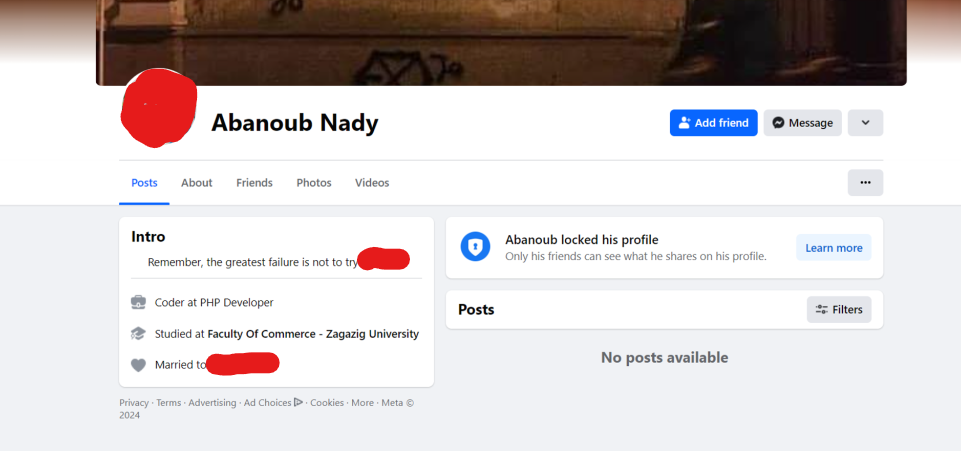
We also found his personal Facebook account.
Finally, using our underground agents and sources, we confirmed the credibility of the data.
Conclusion:
First Name: Abanoub
Last Name: Nady
Nickname: MRxC0DER
Alt names: MRxC0DER-EG, mrxc0derii
Projects: ONNX Store, Caffeine Phishing-as-a-Service Platform
Emails: [email protected], [email protected], [email protected]
Country: Egypt
City: Sharqia
LinkedIn: https://www.linkedin.com/in/abanoub-nady-49baa3237/
Facebook: https://facebook.com/abanoubii
References
- https://blog.eclecticiq.com/onnx-store-targeting-financial-institution
- https://cloud.google.com/blog/topics/threat-intelligence/caffeine-phishing-service-platform
- https://www.trendmicro.com/vinfo/us/threat-encyclopedia/malware/ransom_moware.a



No Comment! Be the first one.