The Ransomware Ecosystem: Roles, Tools, and How Modern RaaS Attacks Work
Ransomware is no longer just a malicious program deployed by a single attacker — it has evolved...
Read MoreSmishing Triad Targets Egypt’s Financial Sector and Postal Services
Recently, during one of our threat hunting operations, our squad identified multiple malicious...
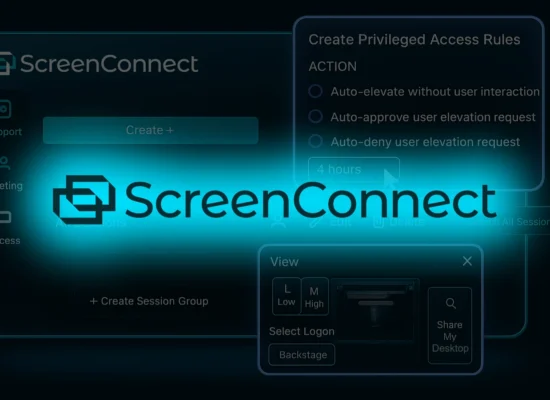
Read MoreSuspicious ScreenConnect Abuse by Threat Actors
Recently observed an uptick in threat actors abusing RMM tools for initial access via...
Read MoreThreat Profile: Conti Ransomware Group
Executive Summary Conti ransomware, first identified in 2019, quickly became one of the most...
Read MoreMuddyWater: Inside Iran’s Persistent Cyber-Espionage Group Targeting the Middle East
MuddyWater, a long-running Iranian cyber-espionage group affiliated with Iran’s Ministry of...
Read MoreMarketing’s Shadow Twin: Cybercrime’s Use of Legitimate Online Platforms
Introduction digital analytics tools—such as link shorteners, location trackers, CAPTCHAs, and...
Read MoreScattered Spider – UNC3944: A Comprehensive and Detailed Threat Profile
Scattered Spider (also known by aliases such as 0ktapus, Muddled Libra, Roasted 0ktapus, Scatter...
Read MoreInfo Stealers 101: Everything You Should Know
In today’s rapidly evolving cyber threat landscape, information stealers — or...
Read MoreBluenoroff (APT38) Live Infrastructure Hunting
North Korean threat actor designations often exhibit significant overlap, making attribution...
Read MoreNobitex Breach: $81 Million Theft Under Investigation
Iranian Crypto Exchange Nobitex Breached in $81M Heist Attributed to Israel-Linked Threat Actors As...
Read More